| Blog - Comodo One News |
|---|
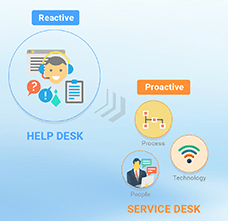
Often the term Help Desk and Service Desk are most of the time perceived as interchangeable, but the two are in fact very different in relation to the extent that they can have an effect on your entire organization. Although they both provide an element of technical support that gets end users back to work, the business consequences of each are affected on comparatively different scales and over varied timelines. Learn More |

Many people might think that IT companies only serve local businesses which can be true to managed service providers (MSPs). Well, technology is evolving and you might be surprised how someone from another state will be able to control your IT requirements. For example, an administrator may be responsible for a network which covers several states and regions and keeping up with all the computers and endpoints can be an intimidating task. Learn More |
|
MSP Delivers Managed IT Services To SMBs and EnterprisesApril 29, 2021

An MSP is a company that provides subscription model to pro-actively manage it's clients' IT environment remotely. It offers a delivery system, application, network, and e-management services, while the customers use a pay as you go pricing model. An MSP handles IT needs for other organizations. It achieves this by providing a range of services proactively, including remote monitoring and management, patch management, and security. Learn More |
|
How MSPs are benefitted using Remote Monitoring (RMM)April 20, 2021

Managed Service Providers (MSPs) offering various IT services often cannot handle everything on their own when it comes to meeting their clientele's requirements. Chiefly because their clientele would be spread out across the globe. Therefore these MSPs cannot rely on a break-fix model when it comes to solving their client's issues. What they need is a dedicated Remote Monitoring Management (RMM) tool. These are endpoint and network monitoring application software which assist managed service providers (MSPs) monitor as well as manage various devices that are a part of a company's IT infrastructure remotely. Learn More |

Any business can be successful only when there is a consistent management of organizational and financial data with efficient information systems. Most of the companies have seen a drift in the process of workflow due to the accuracy and reliability. There is no alternative for the right information at the required time in the world of business where every industry revolves round the Internet of Things Learn More |
|
How to Remote Access a computerOct15, 2018

Many of us who do desk jobs are forced to carry our laptops back to home. But when you know how to remote access a computer it saves a lot of time as it helps to complete your work with ease – typically when you are away from the office. Learn More |
Make sure that your device is up-to-date. Google Play Services should have been automatically installed if you have ever opened the Google Play Store. Sign in with your Google account on your Android device. Most Android users are already signed in, but in case you're not, add your Google account from the Settings menu. Learn More |
|
CRM Software for Your Small BusinessesSep13, 2018

Customer Relationship Management (CRM) is a software solution that brings a range of capabilities all together through a single platform and therefore improve customer satisfaction. It enables the organizations to archive customer details, send emails, generate reports, make calls, plan and schedule appointments, manage and execute a process, all through a single dashboard. Learn More |
|
IT Through Managed Service ProvidersSep20, 2018

Hackers are smarter these days, thereby it is important to implement efficient IT security software that can prevent computer systems from the online dangers. Online fraudsters aim at stealing or damaging the hardware, software or electronic data. Learn More |
|
What is IT SecuritySep12, 2018

Hackers are smarter these days, thereby it is important to implement efficient IT security software that can prevent computer systems from the online dangers. Online fraudsters aim at stealing or damaging the hardware, software or electronic data. Learn More |
|
What is IT Help DeskSep10, 2018

In an enterprise setting, an IT Help Desk Services or IT helpdesk is a place where the enterprise' customers can call to get help with a problem. It is a multi-dimensional team whose primary aim is to help reduce downtime in IT services and operations- making them available for a maximum period of time. Learn More |

Artificial Intelligence (AI), is an advancing technology developed with human intelligence to help machine learn, plan, reason, perceive, or even process human-like language. Artificial intelligence can enhance and strengthen business relationships with customers and therefore boost business revenue. Learn More |
|
Computer-science researchers at Princeton recently discovered that Google services on iPhone and Android devices have been storing your location details even when you have turned off the feature in privacy settings. Location data is always needed for specific Google services such as Maps for providing navigation purposes. Learn More |
Remote Server Administration Tools for Windows (RSAT) is a component of the Windows Server to enable remote management of other computers to run operating system on them. It was first introduced in Windows Server 2008 R2. RSAT streamlines the work of system and IT administrators as it allows the concerned admins to take control of the features and the roles of the admin tool deployed on a Windows Server computer. Learn More |
|
Advantages of Remote Desktop AccessSep03, 2018

Remote access is an efficient and comfortable way for corporate IT personnel to remotely connect to computer interfaces to install and configure software, uninstall software, troubleshoot issues, etc. Generally, it is widely used in the corporates due to the reason that it provides easy accessibility to a computer, device or a network from a remote distance but it also supports the access to home networks. Learn More |

When you are on the verge of choosing a Managed IT Service Provider, it cannot be a random choice, there has to be a thorough understanding about the Managed IT Service Provider from whom you are going to get the service. In this article we will be discussing on how to settle with the right Managed service provider. Learn More |
|
ITIL Service Management ProcessesSep04, 2018
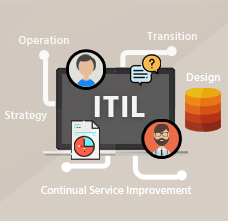
Information Technology Infrastructure Library (ITIL) is a framework containing a set of best practices for delivering efficient IT support services. ITIL enables individuals and organizations to deliver cost-effective IT Service Management and companies adopt ITIL in order to realize their business benefits faster with defined processes. ITIL focuses on resource optimization and regularly reviewing the existing processes in order to gain improvement. It is also capable of acting as a business partner for organizations to adopt only those practices that are applicable to them. Learn More |
|
IT Security ProvidersAugust31, 2018

Cyber threats are on the rise globally, and many businesses are extremely vulnerable to it as a result of ineffective IT security strategies. Security solutions provided by IT security providers are essential for all kinds of organizations, particularly when considering the importance of the internet and the IT systems for running the day-to-day operations of an organization. Learn More |
|
CRM Definition, BenefitsAugust28, 2018

Customer Relationship Management (CRM) software refers to the tools, techniques, strategies, and technologies employed by enterprises for developing, acquiring, and retaining customers. This software guarantees that every single step while interacting with consumers goes efficiently and smoothly in order to increase the overall profits. Learn More |
|
Top 10 Best Network Monitoring Tools of 2018 August 17, 2018
Network monitoring provides enterprises with a comprehensive view of their network and current status, and also allows them to identify ways that will help enhance the overall performance of the processes and address different security vulnerabilities. A Network monitoring tool is capable of permitting Managed Service Providers (MSP) to gain an actual picture of the existing network of new customers, prior to signing a service providing contract. Learn More |
|
Customer Relationship ManagementAugust 17, 2018

Customer Relationship Management (CRM) enables a business to cut costs and increase profits. CRM systems are used to organize, automate, and track business processes like lead generation, marketing, forecasting, sales, ROI measurement, and customer service. Hence, the purpose of a CRM system is to boost integration in these areas and also measure and track the value of customer relationships with the ultimate goals of increased profitability and efficiency. Learn More |
|
Best CRM Software of 2018August 21, 2018

You have probably heard of Customer Relationship Management (CRM) — but what exactly does CRM mean and what is the best CRM software? Let's find out! At a high level, CRM software makes life easier for customer support teams. The aim of CRM software is to better customer relationships; CRM software enables businesses to scale up the process of building better relationships with its customers. Learn More |
|
What is Project Management Software?August 08, 2018

Project management software is software that is used for project planning, resource allocation, scheduling, and change management. It permits project managers (PMs), users and stakeholders to control costs and manage budgeting, documentation and quality management. Project management software is also used for communication and collaboration between project stakeholders. Both free and paid versions of different project management software tools are available and some of the free project management software tools include: Learn More |
|
Virus Removal for AndroidAugust 07, 2018

Virus removal for android is one of the hot topics these days. Cyber attacks have evolved over the years, making them more invincible. To protect your Android smartphone from sophisticated cyber attacks, you need an antivirus app that offers the best virus removal tool for android. Learn More |
|
What is an MSP ? - A Brief DefinitionAugust 02, 2018

A managed service provider (MSP) offers a computing framework platform for the organizations to remotely manage their customer's IT infrastructure. The services may also extend to managing the end-user systems, basically on a proactive basis or under a subscription model. Learn More |
|
What is cyber security all about?June 10, 2021

The term Cybersecurity refers to the technologies and processes designed to defend computer systems, software, networks and user data from unauthorized access; also from threats distributed through the Internet by cybercriminals, terrorist groups, and hackers. Learn More |

Device management is the methodology of achieving the implementation, administration, and preservation of a physical and/or virtual device. Learn More |

Android owns a tool that helps you to locate and remote wipe your stolen or stolen phone. Usually, phones get locked through passwords or fingerprints or patterns in order to maintain the security, but think of a situation in which your phone gets stolen or someone tries to interfere with it. You can put aside all your fears and worries by just allowing Android Device Manager (ADM) to unlock your Android phone. Learn More |
|
Network Management SoftwareJuly 17, 2018

Network management includes an array of methods, processes, procedures, activities, the software, and tools that are used to operate and maintain computer network systems. Learn More |
|
Management Information SystemJuly 17, 2018

The term Management information system (MIS), refers to a computer-based methodology that equips decision makers in an organization with the tools to organize, evaluate and efficiently manage departments. Learn More |
We are living in an age of digital payments. Which usually implies payment via contactless cards. And it seems that the traditional ATM(s) are now facing stiff competition from the newly emerging digital counterparts. Learn More |
|
Top 5 Remote Access Software SolutionsJuly 6, 2018

Remote access software allows you to share files, access other devices on your network and collaborate with ease from virtually anywhere across the globe. Remote access software is primarily used by corporate employees who telecommute and work independently from remote locations. Remote access software can also help IT support teams in managing the devices in their network remotely. Learn More |

There has been no evidence or traces of the recent hacking on the 2016 presidential election, carried out by the Moscow hackers of accessing any of the 350,000 electronic voting machines and changing the number of votes from remote Learn More |
|
Know About Remote Access Software as a Security ToolJune 29, 2018

Remote access solution dates back to 1969 when Telnet protocol was first developed. A couple of decades later, Citrix came into existence to deliver remote access solutions for Windows platforms. With the evolutions of trends and technology PCoIP, RDP, VNC, SSH, XWindows, and others are also added to the list. The benefit of remote access is undoubtedly, the convenience to access the network from anywhere. Learn More |
|
5 keys to enhance Service Desk Agent PerformanceJune 28, 2018

Customers rely on the service desk to troubleshoot any issues. They look at the quality of the service, how well the customer service agent understands the issue, attentiveness, how knowledgeable and professional the expert is and the readiness to quickly solve the issue would elevate the customer satisfaction metrics and add up to more value to the company’s reputation. Learn More |
|
What is Network Security?June 28, 2018

A basic security software solution like antivirus or a firewall is more than enough to protect an individual’s PC. However, in case of protecting business computers which are interconnected within a network, becomes way too challenging. This brought in the inception of Network security to render advanced security options to protect the network from threats Managed Service Providers also called MSPs are separate entities that operate to deliver Software as a Service (SaaS) to provide cybersecurity measures based on the organization’s needs. Learn More |

IT infrastructure management involves many aspects, including management of several policies, processes, devices (like workstations, printers etc.), sensitive information, workforce management and many others. Managing all of them is not an easy task.Because of this, many businesses (usually big ones) seek the help of Managed Service Providers (MSPs). Learn More |

The need for dependable and readily available IT services is growing at an exponential rate as more and more businesses rely on technology to operate. The main aim of modern Learn More |

It's no news that improper patching can lead to security breaches. But despite this, many enterprises choose to suffer such security breaches than apply proper patching. This is because implementing proper security patches with the help of a dedicated patch management software is easier said than done. Enterprises usually employ many software. And keeping track of each and every one of them is often a complex task which costs them a lot of money and time which they rather spend on enhancing their mainstream productivity. Learn More |

For a very long time, IT service management has been recognized as a vital element in the context of delivering and managing IT services. The significance of ITSM in the IT department and their impact on the concept of digital transformation is a topic that is much spoken of these days. Of late, digital transformation seems to be of high priority on the agenda of almost all CIO's. However, there is a growing need to go back to the basis of employing a modernized IT service management strategy (ITSM). Learn More |

With the current climate of consistent digital transformation, businesses are under high pressure to manage and accommodate any quick transition that happens across a range of environments. Implementing IT Service Management (ITSM) tools provide an easy option to oversee and take charge of the change in IT environments. Learn More |

Sometimes we need to access computers remotely from a different location. Like, for example, to access files residing in your workstation located at your workplace. Or to help your dad (who's probably not so good with computers) fix a simple issue. To do this, you need what is known as remote access tools, which let you 'remotely control' another computer, located in another part of the world. Learn More |
|
How relevant is ITIL in Digital Transformation?February 20, 2018

A practicing process like DevOps, Continuous Delivery to transform into the digital world adds value to an organization. The question today is how relevant is ITSM?Technology is an integral part of every business, in that case, how good is IT for any business, even though we see a thin line between the two. They say ITSM is no longer a good thing to have with business, and some say it is good only with the service desk. We all know that ITSM is meant to deliver business capability; it is an enabler to realize real business. Learn More |
|
How to Choose a Managed Service Provider for Cloud MigrationFebruary 16, 2018

The benefits of the cloud have induced many enterprises to migrate to the cloud. Observing the immense benefits reaped by these enterprises, it is encouraging many other organizations to consider moving to the cloud. In many cases, the enterprises have no other option other than to compulsorily move to the cloud in order to stay competitive in the industry. Learn More |
|
The Best Service Desk Software for 2018February 09, 2018

Helpdesk in any company helps to retain customers by providing them prompt services with correct assistance to troubleshoot the system issues. This helps to build brand reputation and also improves good customer experience. The helpdesk system entitles technical experts to instantly respond to a variety of customer issues. This would ensure positive customer feedback and hence help companies maintain a good customer-business relationship. Learn More |
|
The State of the Service Desk Software in 2018February 05, 2018

The climate of digital transformation is on, automated and proactive approach on security would become more critical. The user experiences are getting changed. New advancement in technology and method can empower new experiences that surpass both work and life. Our trust of the organizations we purchase from are much higher than before, while the expectations set on us inside Information Technology are developing as well. So how do organizations guarantee that they stay aware of the competition? Learn More |
|
The Data Breaches Cost of US Businesses in 2017February 02, 2018

With the normal cost of data breaches rising - including per-record expenses of each data security breach - It is critical for organizations to accommodate a serious approach in reconstructing the information security system. As 2017 gets further in our time line as a look back, The recent concern in 2018 is to mandate changes by the way data security is dealt with. 80 percent of review respondents in the U.S and U.K. are looking to change the current IT security approach by either switching to managed service providers or adopting third party resources. Learn More |
|
3 Important Things Windows Patch Management Should DoDecember 14, 2017

A Windows patch management tool that will help you find and utilize patches to keep systems running smoothly, bug-free and safely. Learn More |
|
What is RMM and PSA for MSPsDecember 14, 2017

Combining PSA RMM solution with just one platform, when you were planning out your MSP business. Learn more about PSA RMM solution integration. Learn More |
|
Free Remote Desktop Monitoring SoftwareDecember 14, 2017

Remote Desktop Monitoring Software is the IT tool that helps MSPs to monitor clients endpoint remotely. You can take a look at the advantages of using Free RMM. Learn More |
|
Role of Service Desk in your Business' SuccessDecember 14, 2017

A Service Desk tool which allows MSP’s to implement strong and effective work-flows for business growth. It enables MSP to keep track of all tickets raised by users. Learn More |
|
Advantage of Free RMM Tool Over Paid Tool For MSPsDecember 14, 2017

Learn about the advantages of RMM information when choosing a free Remote Monitoring and Management software to enhance your MSP business. Learn More |
|
How to Read RMM Software ReviewsDecember 14, 2017

RMM Software helps you to manage your enterprise. Here’s the solution to choose the Remote Monitoring Management software products based on reviews. Learn More |
|
What is DDOS Attack?| Types of DDOS AttacksDecember 14, 2017

A Distributed Denial of Service (DDoS) attack in which multiple systems attack a targeted resources and cause a denial of service of the user endpoints. Learn More |
|
Getting Started With Endpoint ManagerDecember 14, 2017

Comodo One ITSM is available absolutely free. It assists MSPs to manage their client infrastructure, by equipping them with necessary IT tools. Learn More |
|
What Makes The Best Help Desk Software? December 14, 2017

The Best Help Desk Software that knows how customer service can make or break a business. Learn More |
|
How Remote Monitoring Tools Benefit Your CompanyDecember 11, 2017

RMM makes everything run smoothly and safely. The program receives real-time information on attempted hacking or breaching activity to the network. Learn More |
|
What is ITSM | IT Technology Management SoftwareDecember 11, 2017

ITSM includes a variety of aspects of IT businesses, such as plan, design, delivery, support, and infrastructure of information technology services. Learn More |
|
How does RMM Work? | Remote Monitoring and Management FunctionsDecember 11, 2017

RMM software is one of the most important tools in IT services and management. RMM are collated IT tools that are loaded to client workstations and servers. Learn More |
|
What's the difference between Help Desk and Service DeskDecember 11, 2017

Are Service Desk and Help Desk the same thing? If not, what's the difference between the two? Learn More |
|
An Easy Guide on How to Enable Comodo RMM | Comodo OneDecember 11, 2017

To enable Comodo RMM, follow the below steps to enable the RMM extension in Endpoint Manager. Learn More |
|
What is ITSM? | Information Technology Service ManagementDecember 11, 2017

ITSM refers to a strategic approach for designing, delivering, managing & improving the way in which information technology is used within an enterprise. Learn More |
|
Improve Your Helpdesk Support Efficiency Using Comodo Service DeskDecember 11, 2017

Comodo Service Desk allows administrators and helpdesk staff to successfully track and attend to user tickets to Improve Your Helpdesk Support Efficiency. Learn More |
|
How Comodo One Can Help MSP(s) Better Serve Their ClientsDecember 07, 2017

Remote Monitoring and Management (RMM) software, which is a part of Comodo One group of products, is a great tool which MSP(s) can use to better serve their client infrastructure in an efficient and seamless manner. Equipped with enhanced remote monitoring capabilities, Comodo RMM helps MSP(s) successfully monitor their client networks against evolving malware and other such IT-security related threats. Learn More |
|
How Enterprises Can Benefit From Remote Desktop ControlDecember 05, 2017

Remote Desktop is the technology administrators use to remotely access user computers present at different locations to fix, update, and carry out other network maintenance activities. Sometimes known as RMM (Remote Monitoring and Management) tools or software, they are widely employed by enterprises globally to run IT administrative maintenance tasks and ensure enterprise networks operate smoothly without any glitches. Doing so, in turn, increases enterprise productivity, as these tools basically optimize the 'enterprise resources' and ensure they are available 24/7 to employees. Learn More |
|
Advantages of Having RMM ServiceNovember 08, 2017

Remote monitoring and management (RMM), also known as network management or remote monitoring software, is a type of software designed to help managed IT service providers (MSPs) remotely and proactively monitor client endpoints, networks, and computers. it's a tool that allows your MSP to efficiently monitor and proactively manage your systems, just like a large corporate IT department would. Learn More |
|
Network Readiness Assessment-What you need to knowNovember 08, 2017

Networks aren't a fixed system - a great challenge to your business's success. They develop, are broadened, tools are upgraded, and new applications incorporated. Modern data networks are ever-changing and the people who worked with it knows exactly the condition of a network. Learn More |
|
The things You Need To Know About Security Patch ManagementNovember 08, 2017

Most of the people that have an idea about Patch management will often see it as a trivial task. They Simply think of it as a click on 'update' and that's it. But in reality, there's a lot more to it and a proper policy is certainly needed. A Security Patch Management Policy is where you can pre-approve the patches that will be installed on your devices on an ongoing basis, based on conditions you define. So what should a patch management policy include apart from deploying patches? Learn More |
|
How does Service Desk bring success to your business?November 08, 2017

A Service Desk is a ticket management system which allows enterprises to implement strong and effective work-flows for internal and customer-facing support departments. The Support Ticketing Management System (also called as Help Desk or Help Desk Ticketing System or Remote Help Desk Support System), enables MSPs (through administrators and help desk staff) to keep track of tickets raised by users, attend to them, reassign them to appropriate department or organizations, and generate reports and more. Learn More |
|
Why do you need Automated Patch Management. Reasons ExplainedNovember 08, 2017

Patching is necessary yet it is also debatable, whether doing it manually or automated is the answer. There are cases against automatic patching but as long as the patching solution reliable, secure, and can be managed easily. It's the benefits that will far outweigh patching by hand. At the very least an Automated Patch Management could pay for itself in reduced man hours within days. Learn More |
|
Right Enterprise Service Desk- How to Decide?November 08, 2017

The business of IT service delivery has changed quite dramatically over the last few years. Data centers are now only part of the story, as hosting services have become more cost effective and efficient in the way they provide platforms and applications. Add to this the simple fact that that every CIO now embraces cloud based applications delivered on multi-tenant platforms by third parties and the BYOD (bring your own device) model that virtually every company now allows. Learn More |
|
Importance of a Customer Service DeskNovember 08, 2017

Once you understand the value of implementing a service desk to manage the flow of requests to and from your customers, there are a number of additional benefits you will start to perceive. 1. You will quickly find that you have a new way of managing the performance of your staff. 2. You will find that you have a way of expressing the value you offer to your customers as a regular report. Reports that help justify the cost.. Learn More |
|
Difference between Help Desk and Service DeskNovember 08, 2017

The concept of an IT helpdesk has been around for decades. And was originally used to describe the physical space where the IT team would sit, and users would either call them or walk up and ask for assistance. Today's process driven central points of support that are manned by IT experts are generally referred to as service desks. Learn More |
|
Effective IT Help Desk Services for your organizationNovember 08, 2017

It feels wonderful when your IT requirements for your business are supported by an efficient and effective IT team. Computers, tablets, phones, networking, storage, printing, applications, licenses all demand tender loving care. They need to be maintained, they need security, then new to be repaired, replaced, updated and provided with supplies. Learn More |
|
What is a Service Desk Software and the benefits it offersNovember 08, 2017

The process of managing requests on behalf of your clients, users and customers may seem simple on the surface but is inherently one fo the most critical functions of any IT support team or Managed Service Provider (MSP). Being able to formally capture the service requests of clients, managed them in an efficient and effective manner, ensure that they are routed to the correct technical or logistical person, and to be able to report on the level of service to ensure that all agreements are adhered to, is critical. Learn More |
|
IT Service Desk Benefits | How they can save your businessNovember 08, 2017

People who administer information technology (IT Admins, System Operators, Database admins, Security admins etc.) know from experience that most questions that they have to answer every day, and ones they have answered before. Every IT expert keeps their own notes on how they solve issues. And possibly one of the warmest feelings the average IT admin ever feels, is that knowledge that once they leave a company, their true worth will be understood,.. Learn More |
|
Increase your cyber security by asking these simple questionsNovember 08, 2017

How to increase your cyber security by asking three easyquestions. Every cybersecurity responsible person knows the power of paranoia. Assume nothing, test everything, and then do it again. Here are three basic questions to ask: 1) How close a relationship does yourcybersecurity provider have with the people who you want to be protected against? If your government will not do business with them because they believe there is a significant chance that they are working with.. Learn More |
|
What is Service Desk? | Features and Benefits of Service DeskOctober 31, 2017

A Service Desk is a ticket management system which allows enterprises to implement strong and effective work-flows for internal and customer-facing support departments. In other words, it helps to communicate with centers that provide a single point of contact (SPOC) between a company and its customers, employees, and business partners. Its purpose is to ensure that users receive appropriate help in a timely manner. Learn More |
|
Importance of Patch Management Software | Why you need it?October 31, 2017

The tried-and-tested practice in the IT industry is keeping your systems updated - always. It's an important decision to have a patch management specialized for your whole company and for your specific IT functions as well. Upgrades for software applications and systems that you have on your computers and network devices are called 'patches.” When you have an ongoing plan for managing patches that can help your business or organization to deal with changes efficiently is a Patch Management. Learn More |
|
What is Patch Management in Linux | Comodo One BlogOctober 31, 2017

Every software demands an update in time so as to be more efficient and effective to out beat the evolving cyber threats. Fixing patches on PCs has been one of most repetitive and tiring errands. Dealing with a software or an application with PCs, running on various working networks, makes it much more mind boggling. Patch fixing is now more straightforward than at any other time. You would now be able to fix PCs running Windows, Mac and Linux from a centralized console. Learn More |
|
What to look for in an RMM Solution | Comodo One blogOctober 31, 2017

There are hundreds of Remote Monitoring and Management (RMM) solutions in the market, each touting to be the best in the industry. This blog will provide you an idea about the essential features that you must look out for, as well as features that would be an added advantage. Now, let us see what is an RMM solution. Learn More |
|
RMM Open Source, Free, What's the Catch?October 31, 2017

Congratulations to your newly opened business! You might be a Lawyer, A Hardware Store owner or a Doctor. Nowadays, no matter what your core business is, there's no denying that technology plays an important role in your daily operations. And as we grow more dependent on modern technologies, system failures are starting to directly impact our ability to do business. Learn More |
|
RMM Software Gives MSP Competitive EdgeOctober 31, 2017

Each Managed Service Provider (MSP) is searching for an approach to emerge as the best in the market. Rivalry is getting savage, and organizations with the most extraordinary client administration will take the upper hand. The utilization of Remote Monitoring and Management (RMM) is essential to increasing your team/clients uptime. Learn More |
|
Get to Know What's a Patch ManagementOctober 31, 2017

An IT service desk is a platform of communication that gives a single point of contact (SPOC) between an organization and its clients, representatives and business accomplices. The reason for an IT service desk is to guarantee that clients get proper help in a convenient way. IT service desk areas are intended to deal with the two episodes and administration demands. In this unique circumstance, an episode is an occasion that outcomes in an interruption in benefit accessibility or quality. Learn More |
|
Definition of IT Service Desk SoftwareOctober 31, 2017

An IT service desk is a platform of communication that gives a single point of contact (SPOC) between an organization and its clients, representatives and business accomplices. The reason for an IT service desk is to guarantee that clients get proper help in a convenient way. IT service desk areas are intended to deal with the two episodes and administration demands. In this unique circumstance, an episode is an occasion that outcomes in an interruption in benefit accessibility or quality. An administration ask for looks for help with a standard errand. Learn More |
|
How to Implement Patch Management SolutionsOctober 31, 2017

Patch Management can be implemented through multiple methods. It can be done quite easily through an automated process or through a manual process. There are advantages and disadvantages for each method of patch management implementation processes. Patch management is a process that involves acquiring, testing, and installing of patches to computer systems. Enterprise computer systems are made up of servers, workstations, laptops, smartphones and other devices connected to the enterprise network. Learn More |
|
Enterprise Network Assessment - 5 Step ApproachOctober 31, 2017

Incorporates the examination of a customer's system foundation, the assessment of its help of vital business needs and proposals for upgrades - without merchant inclination - to meet future necessities. Assets included can incorporate operational appraisal, due tirelessness and designing staff and in addition venture administration and on location outsider. Learn More |
|
Why Network Assessment is NeededOctober 31, 2017

Enterprise networks are built up of numerous entities. Servers, workstations, laptops, tablets, smartphones, other mobile devices (endpoints) and network devices are all connected to the enterprise network. Network Assessment refers to the review of the enterprise/organization IT infrastructure, security, management and the processes involved for network inventory - to identify all the connected entities; network Learn More |
|
Service Desk - Evolution of Ticketing SystemOctober 31, 2017

Service Desk is a ticket management system for organizations. It serves as a single point of contact for all departments within the organization, as well as for clients/customers. Service Desk enables a strong and smooth workflow that tracks all requests provides the current status of the requests and allows all authorized personnel to view the status of the request. The employees of an organization, clients, and customers would hence converge at the Service Desk for resolution of their issues. Learn More |
|
Comodo Provides the Best Patch ManagementOctober 31, 2017

Many enterprises are now learning to invest in good patch management software. Though there are many free patch management options available online, we believe Comodo can help meet your IT requirements. What is Patch Management? Patch management is the process that helps acquire, test and install multiple patches (code changes) on existing applications and software tools on a computer, enabling systems to stay updated on existing patches and determining which patches are the appropriate ones. Essentially, managing patches becomes simple and manageable. Learn More |
|
Small Businesses Can Benefit from Using RMMOctober 31, 2017

In contrast to IT projects that tend to be one-time transactions, MSPs usually charge a flat monthly fee under the subscription model. MSPs often provide their offerings under a service-level agreement. It is a contractual arrangement between the MSP and its customer that enumerates the performance and quality metrics that will regulate the relationship. Learn More |
|
5 Important Reasons Why you need Patch ManagementOctober 31, 2017

Patch Management is most likely ignored among the security topics, but it is an important component of any security plan. Patch Management is the process of handling all the updates of components within the companies information system. These include routers, firewalls, servers, operating systems, anti-viruses, along with much more that could exist within a network. It means that someone is doing just that – managing these patches. Learn More |
|
How To Ensure Your Network Is Properly Patched?October 19, 2017

Making use of a patch management tool doesn't necessarily mean all the systems in your network have been properly patched. Because no matter how technically-equipped the patch management tool you may be using might be, it will be of no use to you without a solid patch management strategy in place; in other words, if no proper security policies form a part of that strategy. Learn More |
|
Importance of Having an Effective Patch Management StrategyOctober 07, 2017

Patch Management has its own relevance in cyber security; it addresses those vulnerabilities in software and systems which cyber criminals would make use of to gain entry into systems and networks and then steal sensitive personal data or lock users out and demand ransom. Yes, effective patch management is key to cyber security. Businesses today are prone to all kinds of cyber attacks; hackers would constantly be on the lookout for software/system vulnerabilities that are not patched. Thus it becomes important that every business today has a proper patch management strategy so that cyber criminals are kept at bay exploiting security holes. Learn More |
|
7 Ways RMM Software Can Help Increase Efficiency of IT teamSeptember 28, 2017

Technology today is evolving and multiplying in the enterprise scenario, in complexity as well as in profusion. Today we have the BYOD (Bring Your Own Device) technology, the IoT (Internet of Things) and such other things which have revolutionized everyday infrastructure at the enterprise level. IT management for organizations has changed, drastically with the introduction of mobile technology and personal devices into the work culture and with the issues too becoming very complex and sophisticated. IT is now strategic in any enterprise and the CIO is as important as the CEO or CFO. Learn More |
|
Patch Management for Tackling Ransomware Is Easier Said Than DoneSeptember 19, 2017

In the connected world of today, there are many avenues for cyber criminals to try penetration. The increasing development of ransomware and ransomware-as-a-service has led to massive outbreaks in the number of attacks. Every time a vulnerability has been exposed and an exploit detected, security firms and application developers develop and release appropriate patches to thwart further exploits. Patches are released periodically or as hotfixes. These hotfixes are urgent security patch updates that must be applied without any delay. Learn More |
|
Why You Need To Secure Your Endpoints Comodo ONE BlogSeptember 14, 2017

It raining security threats in the digital world. Security threats which are so severe in nature that they not only bringing the digital world to a standstill but are making us revert back to using papers for carrying out our day-to-day operations as our computers recover from these malicious security attacks. Therefore the need of the hour is to equip our networks using the right combination of security tools which can resist such attacks. Learn More |
|
The Top 3 Free Email Marketing PlatformsSeptember 11, 2017

Email marketing is dead and gone. It's 2017, social media is the best way to engage with your audience. It is 2017, but email marketing is not dying. According to Campaign Monitor, you are 6x more likely to get a click-through from an email campaign than you are from a tweet. Research by Randicati said a message is 5x more likely to be seen in email than through Facebook. In fact, email marketing has an ROI of 3800%. Yes, you read that right, three zeros. Thirty eight thousand. Learn More |
|
And The Academy Goes To...September 11, 2017

In case you missed our recently published press release, we at Comodo have launched a free self-paced and interactive education portal for MSP partners, Comodo Academy. Here, partners are trained and certified on the Comodo ONE platform for IT and security management (ITSM). The online portal contains tutorials, quizzes and practical exams to expand a partner's security knowledge. Learn More |
|
What does Comodo One and iTunes Have in Common?September 11, 2017

Why is Comodo One free? What's the catch? When is my free trial over? The answer: To put it plainly: We, at Comodo One, would like to partner with your MSP business. You don't make any money off of management tools, so why would we charge you for them? Instead, we will help you manage your IT infrastructure. Then, you'll be able to purchase our apps, which you can sell to your clients as part of your successful business services. When you make money, we make money. It's really that simple. Learn More |
|
Pathways to simplify and Speed Up Security Patch UpdatesSeptember 07, 2017

Patches are inevitable security for all software applications. Ensuring updated patch security is possible only through effective patch management. Cyber security threats are constantly evolving. While on one side cyber security professionals are trying to make the internet and IT world more secure, on the other side cyber criminals are trying to find out ways to identify new vulnerabilities and penetrate the defenses to eavesdrop, compromise and steal data. Learn More |
|
Comodo One Endpoint Protection | Stay Ahead of Unknowm ThreatsSeptember 05, 2017

The Comodo One approach denies unknown files defaultly, while also allowing the user to safely access it. Think of it as putting your unknown file in a little jail cell. You can still interact with it, but it's unable to roam freely until it has been deemed good or bad. Comodo One is the only endpoint security solution that automatically handles unknown files and zero-day threats with a default deny approach. Almost all antivirus solutions default allow unknown files, which allows malware to go into the system/network completely undetected. Learn More |
|
Specialized Threat Analysis and Protection(STAP) | Comodo OneSeptember 05, 2017

Cybersecurity, like all technology, is constantly changing. Step by STAP. If you don't know what STAP is here's the lowdown: it's a term IDC coined that stands for Specialized Threat Analysis and Protection. STAP is meant to detect zero-day attacks and data exfiltration by attackers, which can go on undetected for weeks, if not years. Basically, it's a new category of security products which aim to defend against specialized threats that have emerged over the last couple years. Learn More |
|
How to Convince Your Break-Fix Clients to Sign Up For MSP?September 01, 2017

Transitioning your break-fix clients to managed services can be a challenge. Most people live by the 'if it ain't broke, don't fix it' rule. Why? Because people don’t like to spend money on what-ifs. Usually... Americans spend thousands of their hard-earned dollars on auto collision insurance annually. In reality, the average person is far more likely to have their computer crash than their car. Rationally, the SMB owner knows that to get the most out of their network, it needs to be monitored and maintained. But when it's time to part with their money in order to prevent something that might happen, suddenly they tighten their purse strings. Learn More |
|
Basic Tools for True Managed Service Provider(MSP)September 01, 2017

With a new major cyber attack hitting computers worldwide every week, business owners are wondering if there are any safe zones in cyber warfare. While some businesses are at a larger risk than others, everyone needs some kind of internet protection. That's where you come in. Managed Service Provider to the rescue! But are you a true MSP? There are basic tools you need to employ in order to truly fit the mold and ensure your business is secure from hackers' reach. Learn More |
|
Top Customer Referral Methods to Increase Your MSP BusinessAugust 31, 2017

While there are ways to increase your MSP business without prospecting (link to other blog post), one of the most beneficial marketing techniques to consider is referral marketing. Generally, referral marketing will generate more positive results and higher sales compared to pursuing cold leads, because the business-customer relationship is jumpstarted. Referrals let you leverage credibility from your existing customers in order to build trust with new customers quicker. Learn More |

For one reason or another, many people are still living under the misguided notion that their information is safe on their electronic devices. It's certainly less stressful to pay no mind to hackers, viruses, scams and breeches, but it is dangerous. As an IT service provider, you know that, but your client Jimmy, the small business owner, doesn't. At least not yet. Cybersecurity isn't a tangible threat; there is no robber entering Jimmy's office, stealing his computer and leaving everything he worked so hard to build in shambles, but there may as well be. Learn More |
|
The Need for Best Practices in Patch ManagementAugust 30, 2017

Patch Management may seem dreary and boring. But it is not something to be taken lightly. Patch management is of paramount importance to the overall security of an IT enterprise. In any IT system, patches can be updated automatically as well as manually through patch management software. In a large enterprise, if you are an IT administrator, it would be your responsibility to download necessary patch updates to the server and then roll out the patches to the endpoints based on defined policies. A patch management system, hence, plays a vital role. Learn More |

Congratulations! You are utilizing one of the most successful (and underrated) marketing strategies of the 21st century! You know that buyers consume content before making a purchasing decision - in fact, 47% consumed 3-5 pieces of content before taking the first step towards making a purchase. The biggest hurdle any business has to overcome is building trust with strangers, and blogs are an excellent way to do that. If you invest the time in maintaining a blog with your current and prospective clients, the ROI will be incredible. Learn More |
|
How to Keep the Internet 'Bad Guys' OutAugust 24, 2017

What's the problem with the state of antivirus solutions today? Why is patch management so important? They say... Keep your operating system and software up to date.Don't click on suspicious links. Don't open emails from unknown senders. But that's more difficult a proposition than it may seem. You want to be setting your people up for success. But just like anything in life that requires changing of behavior, if you need to rely too heavily on attention to detail and constant willpower, you can't sustain long term success. In this case being prevention of the slightest cyber vulnerability. Learn More |

This climate denotes a critical defining moment with respect to overall digital hostility. The monstrous ransomware attacks on May 12 started in Europe and spread over the world contaminating more than 300,000 PCs in more than 150 nations. Those contaminated were gone up against with messages to pay $300 in bitcoin to open the documents on the tainted PC. The programmers were playing the rates that some number of PCs would not be legitimately fixed. Learn More |
|
4 Invaluable RMM Vendor Value-Adds MSPs Need Right NowAugust 09, 2017

Remote Monitoring and Management (RMM) tools help MSPs run their businesses smoothly in two ways. First, they keep track of all the client devices subscribing to the MSP's services. Then, they also execute management tasks like patching updates and other such administrative tasks for the MSP's clients. As a result of these two key operations, the workload of MSPs reduces greatly, allowing them to focus more on the quality of the services they offer. Unfortunately, the general perception among MSPs is that the services of RMM end here; that they do not extend beyond keeping a tab on devices and executing administrative tasks. Learn More |
|
Pause Windows Patch Update From Command Line PromptAugust 04, 2017

Let's face it. We all find Microsoft Windows Updates annoying at some point of time. Of course, there's no denying that these days Microsoft is making every effort to improve user experience and security by providing patches which fix bugs and introduce new functionality into its products, but the fact that these patch-related reboots, can sometimes occur at very inconvenient times, is something which cannot be totally ignored. Learn More |

How do we make sure that all the endpoint is protected with AV? Well, for every organization to have an Antivirus for every endpoint will be quite a challenge. Now that we have the option of MSPs, there are enough chances for customers to have AV from different vendors. This happens often nowadays when MSP gets a new customer when endpoint protection is not done properly. Not to mention the risk when the large network has a compromised endpoint. Learn More |

Selecting a Remote Monitoring and Management (RMM) tool involves two critical factors. One is getting the right technology and two is ensuring whether your provider is able to meet your current as well as future requirements. If you can find a vendor that is easy to work with and at the same time offers flexible solutions. Moreso, they that make delivering your managed services more efficient, then you are on the right track. Learn More |
|
How To Convince Break-Fix Clients to Sign Up For MSPJuly 19, 2017

Transitioning your break-fix clients to managed services can be a challenge. Most people live by the 'if it ain't broke, don't fix it' rule. Why? Because people don't like to spend money on what-ifs. Usually... Americans spend thousands of their hard-earned dollars on auto collision insurance annually. In reality, the average person is far more likely to have their computer crash than their car.Rationally, the SMB owner knows that to get the most out of their network, it needs to be monitored and maintained. But when it's time to part with their money in order to prevent something that might happen, suddenly they tighten their purse strings. Learn More |
|
Patch Management BasicsJuly 18, 2017

Patch management is the process of installing (and managing) the latest patches - code changes which improve the system or fix security vulnerabilities - on various systems within a network. Tasks like deciding what patches are appropriate for particular systems, ensuring these patches are installed properly, testing systems after installation, all fall under patch management. The objective of patch management is to keep various systems in a network up-to-date and secure against various kinds of hacking and malware. Learn More |

Patch Management is a tool that assures security to streamline the functioning of corporate software. New patch updates are to be fixed now, so as to avoid the interference of malware through outdated applications or software. Best practices propose to automate patch updates as and when the patches fixes are updated. Security is always going to be a cat and mouse game because there'll be people out there that are hunting for the zero day award, you have people that don't have configuration management, don't have vulnerability management, don't have patch management. Learn More |
|
Top Online Managed Service Provider (MSP) ResourcesJuly 18, 2017

As an MSP, it's crucial to stay up-to-date on the latest tech trends, products, breaches and marketing strategies. Staying informed on all of the latest developments in the constantly changing internet security sphere isn't easy, but it will help you deliver excellent service and protection to each of your clients. You'll hone your skills and learn how to market yourself better by recognizing trends and avoiding common errors. Remaining an expert in your field requires research and lots of reading. We know you have other things to worry about besides looking for the most reputable sources, so we put together this list of our favorite MSP sites that help us stay current. Learn More |

There are three key factors for the success of managed security services. Any managed services provider (MSP) who wants to provide security-as-a-service offering and wants to be successful must strongly build upon these three key factors - skilled personnel, advanced technology, and employee education. The role of an MSP has drastically changed over the last 20 years. The rapid increase in digitalization, cloud computing, skilled IT personnel, and more sophisticated cyber attacks have made businesses subscribing to MSPs to ramp up their demanding expectations. Learn More |

MSPs (Managed Service Providers) which deliver IT network, application and system management services cannot survive on their own. Chiefly because their clients are many and usually spread across the geographical area. Therefore if these MSPs wish to function efficiently, they cannot do so without the help of remote monitoring software - also known as remote monitoring and management tool. What Does Remote Monitoring Software or Remote Monitoring Management Tool Do? Remote Monitoring Management (RMM for short) tool helps these MSPs become more efficient in servicing their clients by providing them with remoting capabilities. Learn More |

If you're a managed service provider (MSP), then you want to take your business to the next level. Unfortunately, even if you are the smartest, best-trained, hardest working internet security provider in the industry, you'll still struggle to propel your business onwards and upwards. Why? Because it's not about how hard you work. It's about how smart you work. Why? Because it's not about how hard you work. It's about how smart you work. If you aren't using the right RMM tool to facilitate your expertise, you're going to work harder than you need to, and you're going to make less profit than you should be. Learn More |
|
Free Up Your Business Using RMM SolutionJuly 04, 2017

This Independence Day Free up Your Business with RMM, July 4th is historically important for Americans. The day marks America's departure from the British Empire. The day commemorates the adoption of the Declaration of Independence. Since that day, July 4 has become a federal holiday in America, with celebration and events across the country. Festivities are distinctly patriotic, marking the importance of this holiday for national identity. Reap Rewards of RMM, There's nothing as American as A baseball cap, Soccer, Apple pie; and a Fourth of July cookout, and other hosts of events on Independence Day. Learn More |
|
Top 4 Key Factors to Choose RMM and MSPJune 21, 2017

Remote Monitoring and Management Software intends to help and oversee (MSPs) Managed Service Providers from remotely and proactively screen customer endpoints, systems and PCs. This is additionally now referred to as remote IT administration. Four key factors to choose Remote Monitoring and Management and Managed Service Providers.Automatic Management System: The powerful ingredient with current MSPs is in delivering automated platform to stabilize IT operations and management instantly routing to scale up and meet the client's needs. Computerization is rapidly turning into the most powerful ingredient for current MSPs. Learn More |
Offering break-fix solutions through Remote Monitoring and Management (RMM) is an easy way to get more new customers. It has wrongly been perceived that offering break-fix solutions is not a good business model. Many customers still don't understand the advantages of a managed service solution. One main factor putting them off is the cost involved. Industry experts have suggested that offering RMM for free is an even better approach. Many managed services providers (MSPs) have learned it the hard way, after losing customers who wanted only break-fix support. Learn More |
|
How MSPs Can Use PSA and RMM Tools to Save TimeJune 14, 2017

MSPs (Managed Service Providers) help their clients earn more revenue, expand business and manage lots of things, using PSA (Professional Services Automation) tools and RMM (Remote Monitoring and Management) tools. Their focus is always on helping clients simplify their operations, maximize efficiencies and thereby enhance their productivity and profitability. However, it's to be noted that these PSA tools and RMM tools can help the MSPs save and find extra time each day. Here are three key tips on how to achieve that... Learn More |

It's 11 o'clock on a Monday morning. The office branch manager is in a fit of rage. He's been waiting for 2 hours for an important email, but he is not yet in receipt of the email. Again it looks like the mail server is misbehaving, and the delay in getting the mail will only prolong. The admin guy makes a quick analysis and confirms that no email is jammed in the email server. So what’s the exact problem? Learn More |

Lack of trained IT professionals and insufficient budget are plaguing the health care industry with massive cyber security incidents. The latest WannaCry ransomware epidemic in May 2017 infected over 230,000 computers in over 150 countries. The National Health Service (NHS) in Britain, was severely affected. It was initially believed that the attack had been targeted at the NHS, but it was not so. The attack infected systems across the UK, Russia, Spain, India and China. This should offer some sort of relief for the NHS that it was not being specifically targeted to them. Learn More |
|
Trending Report: The Essential MSP ToolkitMay 31, 2017

What all must you have as part of your MSP tool kit arsenal? If you have in the Managed Services Provider business and has been serving numerous clients for quite some time then you must be using numerous tools that enable you to provide easier and better management. Having numerous tools is fine are they serving the purpose? Are they easy to use? Are they enabling secure management? Are they providing value? Learn More |

For companies of all sizes from small family businesses and startups to major enterprise businesses and global corporations, technology is changing the way daily business is conducted. This is both an evolution and a revolution, opening up the potential for greater automation, increased security as well as lower cost for companies. Companies that can embrace these changes and maximize the use of technology can streamline the business, saving costs while also utilizing the latest in software to help them to be more efficient. Learn More |
|
How MSP's Can Gain More Clients Using AIDAMay 16, 2017

Adapting to managed services from a fixed model has become a necessity in the evolution of your IT business. In the recent years, the industry has seen a surge in the adaption of Managed IT services. Now IT decision makers and business owners want to explore on how a managed service can be beneficial for their operations. It has been noted that there is a huge demand in adapting MSP for businesses. Since every business is becoming increasingly specialized, the same also goes for Managed Service Providers. They have already started offering specialized services for a certain type of business, and their focus is to stay relevant in the ever-changing world of IT service. Learn More |

Finding a way to be able to generate leads and expand a business has always been a problem. For any company offering remote monitoring and management as a Managed Service Provider, finding a way to reach out to new customers and clients can be a very particular challenge. Cold calling is always difficult as it can be a hassle just to find out the small to mid-sized company structure to determine which person is in charge of technology. Then, to make matters even more complicated, it can be difficult to try to explain the advantages of MSP and remote monitoring and management technology with enough detail and not too much technical jargon to highlight the benefits of this system. Learn More |
|
RMM or PSA: Which is Best for an MSP?April 25, 2017

If you are starting an MSP, this is one question that you need to ask yourself- PSA or RMM? PSA (Professional Services Automation) and RMM (Remote Monitoring and Management) are basically related to MSP business and also concern people going in for a shift from break/fix to MSP or transitioning from being a sole practitioner to hiring a first employee. When business is thus evolving, it has to be decided whether to go for PSA or RMM. Let's explore both PSA and RMM in detail... Learn More |

The managed services market is estimated to grow and thrive into a business worth $242.45 billion by 2021. With a compound annual growth rate of 10.8%, it is no surprise that more and more businesses are adopting for managed service providers or MSPs and RMM software is more a need rather than a luxury. Let's analyze a few trends and facts that the industry is supposed to concurrently witness. Learn More |

Remote monitoring and managing (RMM) software are a type of application used by IT service providers to maintain and manage the IT estates of their clients. The main objective of RMM platforms is to ensure tabulation of the client’s IT systems and its components including servers, desktops, applications and mobile devices as well. Also, RMM tools help with the efficient execution of maintenance of IT estates. Functions such as patching, software updates, configurations, and other such repair and up-keep functions can be done through remote locations rather than on-site. Learn More |

Data centers are very big business. With the data protection landscape changing rapidly, data center business will continue to grow further. The challenges involved are immense and are destined to become even more so in the future. Monitoring is very critical in data centers and reputed data centers monitor every detail diligently. There are many data center infrastructure management (DCIM) software packages available in the market. However, many have not been successful as they have not been able to meet the meticulous monitoring demands spelled out by data centers. Learn More |
|
Patch Management can Prevent Security BreachesMarch 24, 2017

Software and Applications are developed to benefit the users. However, users identify flaws only while implementing it to benefit the purpose. Such flaws create a path for the hackers to access the vulnerable application to exploit and extract valuable information. Software vendors release security patch fixes to fix such vulnerable issues. IT departments and individual users most often retard to update the software to fix the latest patch and hence stay vulnerable and best target for a security breach. Learn More |
|
Evolution of the Powerful and Secure Service DeskMarch 22, 2017

For any organization today, demands of digital business would exert great pressure on the service desk, wanting it to become more responsive, more efficient and at the same time drive down costs. All this happens at a time when cyber attacks are on the rise and are threatening all kinds of businesses, big and small. Today it's important for companies to use automation for accelerating the ability to respond to tickets. At the same time, it would indeed be great if a company could also close the loop and use automation to help deploy changes as well, especially those that might help remediate vulnerabilities fast. This helps companies save on costs and save or build up their brand reputation as well. Learn More |

Digital healthcare is taking a new turn and approach in handling the healthcare products and services. There are healthcare apps to improve the lifestyle. There are home monitoring devices implements Remote Monitoring Management that can be used by clinicians to interact with patients and analyze their signs of health progress from remote. However, whatever the technology solutions evolve, there can never be a magical remedy to cure any ailments. Learn More |

As per reports attackers have used a content-injection vulnerability (in WordPress 4.7 and 4.7.1) recently disclosed and patched in WordPress 4.7.2 to deface over 1.5M websites. Experts say that this vulnerability, which is an unauthenticated privilege escalation vulnerability in a REST API endpoint, is one of the worst WordPress related vulnerabilities to have emerged in some time. The issue was patched silently and mention was made in an update in the 'WordPress 4.7.2 Security Release' dated January 26, 2017. The update says- An additional serious vulnerability was fixed in this release and public disclosure was delayed. For more information on this vulnerability, additional mitigation steps taken, and an explanation for why disclosure was delayed, please read Disclosure of Additional Security Fix in WordPress 4.7.2. Learn More |
|
Digital Transformation To Secure Connected EnvironmentFebruary 27, 2017

Digital transformation of businesses is the trend today. Processes, workflows and business cultures are today transformed to suit digitalization. Companies now sell products/services online, create mobile-friendly loyalty programs/coupon apps, automate quality assurance and testing programs, leverage IoT (Internet of Things) to make the most of the trend and adopt cloud platforms to handle quotes, pricing, orders etc. Learn More |
|
The End of Patch Tuesday and its ImplicationsFebruary 20, 2017

Well, Microsoft ends its monthly Patch Tuesday security bulletins (also known as Update Tuesday) this month, replacing them with a new online database, plus automatic updates on Security Updates Guide. Microsoft had announced this in November itself in a blog post- "Security update information will be published as bulletins and on the Security Updates Guide until January 2017. After the January 2017 Update Tuesday release, we will only publish update information to the Security Updates Guide." Learn More |
|
San Fransisco Muni Ransomware Attack | What to Learn from Such HacksFebruary 10, 2017

We live in a world where malware and malware attacks are very common. The latest buzz in the malware world mostly concerns ransomware, which has been seen to cripple organizations and companies and forces them to pay ransom to get back on track again. It was in November last that San Francisco's Muni light rail public transportation system fell victim to a ransomware attack. This high-profile ransomware attack, as later revealed to the media by the attacker, was not pre-planned or deliberate. Learn More |
|
Micro Data Centers are Important for Digitally Connected EnterprisesFebruary 06, 2017

This is the era of IoT (Internet of Things), BYOD (Bring Your Own Device), RMM (Remote Monitoring and Management) and such other things that point to the relevance of digitally connected enterprises. In this scenario, it's the processing and storage of data that needs to be discussed the most and which also needs to be taken care on in the most professional of manners. Learn More |
|
How To Retain Traditional Cybersecurity MeasuresJanuary 09, 2017

Things are changing fast, as regards cyber-security, just as in other walks of our day-to-day life. Cyber security threats are becoming more and more sophisticated in nature, and more and more cyber attacks are happening all around, even targeting government agencies and high-profile organizations. There are even instances when cyber attacks originate from people inside an organization. Cyber security strategies too are changing and are becoming real sophisticated, but the belief nowadays is that no layer of security can perhaps assure and ensure total security. There is the thought that almost everything is accessible today and any intruder can get it, despite going for the best of security measures. Learn More |
|
Role of Automation Software In Retail IT channelDecember 30, 2016

RMM automation software offer many business benefits to the retail IT channel and hence they are now adopted and implemented by many businesses. They help businesses run more efficiently and be more agile and cost-effective. They also help businesses gain confidence in the security and the performance of their infrastructures. Let's take a closer look at what all the benefits of using RMM automation software are- Learn More |
A managed services provider (MSP) must endeavor to provide better services. As in all businesses, collecting and analyzing the data is very important as it would help in improving the total business process and provide a better experience for its customers. In the end it should lead to increased revenue and expansion. Business data analytics is a must needed weapon for MSPs to survive. To this end, businesses must adopt automation for better capturing of data involved. Business services automation requires professionals services automation (PSA) or Services Help Desk Management, along with remote monitoring and management (RMM). Learn More |
|
Patch Management | The Benefits and Increasing Security EfficiencyDecember 09, 2016

Do you know nearly all data breaches happen at least one year after a specific vulnerability has been made public and proper patch management could easily prevent these problems? This is according to a recent data breach report from Verizon. In fact most of these vulnerabilities are known and there are patches available, so why do so many companies appear blind to these vital security issues? Let's delve into this subject a little deeper, explore the benefits of this strategy etc. Learn More |
|
Remote Monitoring and Management (RMM) for Cloud SecurityNovember 28, 2016

Today when internet connected devices are so integral a part of our day-to-day lives, it's a real digital transformation that's happening all around. Businesses are making the most of this scenario, but at the same time, there are complexities associated with this kind of digital transformation that businesses need to understand. Most of these complexities pertain to security, and security is something that always has a direct impact etc. Learn More |
|
Identifying a Safe and Smart RMM platformOctober 31, 2016

Remote Monitoring and Management (RMM) is an emerging trend now. MSPs (Managed IT Service Providers) use RMM tools to remotely manage and monitor client systems and networks as well as the endpoints on the clients' side. RMM also helps MSPs in gathering information regarding applications, hardware etc, all operating from the client's location and also in obtaining activity reports. RMM, which can be carried out from a single, unified dashboard, helps manage or solve issues, do trouble ticket tracking, remote desktop monitoring etc and remotely install software and updates, administer patches etc. Learn More |
|
Remote Monitoring and Management: The Emerging TechnologyAugust 03, 2016

Remote Monitoring and Management (RMM) is the technology of developing software or information technology tools which would help Managed IT Service Providers (MSPs) engage in remote monitoring of client systems and networks plus the endpoints on the clients' side. Using these RMM tools MSPs can gather information regarding applications, hardware etc which are operating in the client's location and also obtain activity reports. Thus Remote Monitoring and Management helps resolve issues and do things like trouble ticket tracking, remote desktop monitoring etc and remotely install software and updates, administer patches etc. Learn More |
CLOUD BASED IT MANAGEMENT SOFTWARE FOR
MSPs and ENTERPRISE
Remote Monitoring and Management | Service Desk | Patch Management
Now Add Up To 50 Devices for Free