cWatch Network Security
Real-Time Threat Intelligence, Not Just Alerts
Why cWatch Network Security?
cWatch eliminates corporate breaches by monitoring all network traffic, by blocking all malicious and potentially malicious executables, and by providing immediate alerts to administrators.
cWatch offers an efficient solution for managing advanced IT threats to an organization. It is a single security product that has the capabilities of multiple security systems.
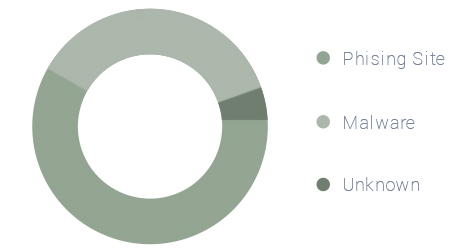
Network Threat Detection Process
cWatch displays the detected network threats on the Dashboard as a part of the statistical summary of detected threats, top 10 untrusted domains, version, information, hardware details and system information.
The details of detected threats - both unknown and malware - for the current date are displayed on the 'Network Threat Detection' graph.
Comodo entwines smart cyber defence features through its security intelligence and event management product (SIEM) - cWatch Network.
Comodo cWatch Network is an approach to security management that orchestrates to strengthen organization’s information technology security. It stands the only source, which is all encoded with the following resilient features in relevance to the MSPs' demand to help them up scale the business:
Features
- Real-time processing and monitoring of incidents
- Continued Possession of logs, cataloguing and backup of data
- Pre-set queries to address typical use-cases
- Efficient and user-friendly Interface to forge custom queries
- Configurable dashboards
- On-demand report generation and scheduling
- Incident Management
- Option to choose between agent-less and agent log collection
- Customer-relevant policy generation and management
- Instant alerts and incident assignment
- Up to date Lists of parameters based on the incidents that to be used in queries and rules
- Prompt search process over huge magnitude of data
Virtual risks abuzz amidst the enterprises, Comodo cWatch takes a competitive edge to outplay today's competitive adversaries to be the best source for threat monitoring. It aids to identify the incidents that are most insecure and unfavourable to your organization. Avail real-time advice on possible threats, probing a heads-up for fast action against the threatening incidents from the netherworlds.
Delivers Proactive Security Approach
Comodo cWatch Network Sensors persistently monitor system and network activity to detect if there exists any invading malicious activities or violations of policy through the organizations' network. It ventures to foster a proactive network security monitoring approach that encompasses thorough analysis of all network traffic.
Performs Full Packet Capture
It is devised to execute full packet capture. It works to incorporate comprehensive real time incident monitoring, interpretation of adverse incidents and forensic analysis after an attack.
No Interference on Production Networks
It runs inspection when duplicated traffic is detected, with absolutely no interference of malicious threats like Advanced Persistent Threat (APT) on the production networks.
